In this four part series I will be going through implementing Microsoft Remote Access Server /VPN only solution on Windows Server 2016 and integrating it with RADIUS / NPS server for Authentication then add on it Azure MFA implementation for second/Multi Factor authentication for VPN Users as sending message or getting a call on your cell phone.
So in Part 1 of this series we installed and enabled the VPN only role on our Windows server 2016 box. In the next part we will start configuring the VPN properties and integrate it with our RADIUS server. Hopefully you enjoyed this part and see you on the next part.
Part 2 of this series http://itcalls.blogspot.com/2016/10/implementing-microsoft-remote-access_30.html
Part 3 of this series http://itcalls.blogspot.com/2016/11/implementing-microsoft-remote-access.html
Part 4 of this series http://itcalls.blogspot.com/2016/11/implementing-microsoft-remote-access_5.html
So Why VPN solution ? Microsoft have a very nice solution for Enterprise customers named DirectAccess (Will have a series of articles on its implementation in Server 2016) however it has some requirements on top of them to be corporate domain joined and its not available for all windows Versions (Only Enterprise ones).
Traditional VPN fills this gap by targeting any windows version as Home and Professional and at the same time you can launch it from your home computer, tablet or mobile to connect to your corporate network. This will be very helpful especially nowadays more and more companies are supporting the idea of Bringing Your Own Device (BYOD) which of course can be any version of Windows and its not member in your domain.
Another question will be can I have one server with both VPN and DirectAccess roles co-existing together ? The Answer is Yes however one draw back is that you will loose the Null encryption and you will have to pay the penalty of the DirectAccess IP-HTTPS double encryption. In our Scenario I will go with installing the VPN role on a single server without other roles.
In Part 1 of this series, we will install the VPN Server, configure it and Enable it.
Part 2 of this Series will continue with configuring the VPN properties, integrating it with RADIUS server for authentication.
Part 3 of this series We will configure the VPN on the client machine and deal with common issues and frequent questions as accessing your Shares, DFS root from your VPN client.
Part 3 of this series We will configure the VPN on the client machine and deal with common issues and frequent questions as accessing your Shares, DFS root from your VPN client.
In Part 4 of this series we will configure Azure MFA to add second level of authentication for VPN users connecting to our VPN server.
So let us get started by installing our VPN Server on our Windows Server 2016. This Server is 2 NIC server with 1 NIC in our Local Network and the second NIC in the DMZ
For 2 NIC server (Multi-homed server)we need to make sure of the following configuration:
For 2 NIC server (Multi-homed server)we need to make sure of the following configuration:
- You have only one Gateway which will be on the Second NIC (The one on DMZ or External Network), the Internal NIC will have no Gateway.
- DNS servers will be specified on your internal NIC (This will be your internal DNS servers)
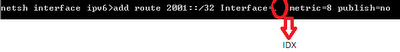
- If you have multiple VLANs on your network, you won't be able to reach them from your VPN server since there is no Gateway on your internal NIC. You need to create static routes on the VPN server to these VLANs, For example if you have specific Servers subnet or other subnets as Printers or specific group then you need to create persistent route to this subnet (ROUTE ADD)
Implementing and Configuring VPN on Windows Server 2016 Standard.
- Open the Server Manager on your Windows 2016 VPN server and click Add Roles and Features.
- Click Next and pick Role based or Feature based installation
- Ensure Select a server is your option and your server name is displayed and highlighted in the Server Pool below area
- Select the Remote Access Role
- Click Next - Add features and then select the first option Direct Access and VPN (RAS) as per the below screen shots
- Click Next for the Web Server (IIS) role installation (This is mainly needed for your Direct Access implementation - Don't forget we picked the role that allow us to install both options, VPN and Direct Access). Click Next on the next screen for the IIS roles services.
- Confirm all your settings and check the Restart the destination server if required and go ahead for Install - It will take few minutes for the installation.
- After Installation is done you will get the option to configure the server with the warning sign displayed in your server manager as shown below. I would highly recommend not doing it this way so you can have better and full control on your configuration
- Instead from Tools, open Remote Access Management - Direct Access and VPN - Pick the second option Run Remote access setup wizard and choose to deploy VPN only
- Right Click on your server name - Configure and Enable Routing and Remote Access - Choose Custom Configuration - VPN access and click Finish (Check below screen shots)
- Your services will restart and the Remote access Service is up and running now and ready for configuration and Usage.
Part 2 of this series http://itcalls.blogspot.com/2016/10/implementing-microsoft-remote-access_30.html
Part 3 of this series http://itcalls.blogspot.com/2016/11/implementing-microsoft-remote-access.html
Part 4 of this series http://itcalls.blogspot.com/2016/11/implementing-microsoft-remote-access_5.html